Vulnerability Management : Your Key To a Safer Digital World!
Introduction
In today’s interconnected world, managing digital vulnerabilities is similar to protect your network against potential threats. Vulnerability management is the process to involves finding, assessing, fixing, and reporting on security weaknesses in systems and software’s. It’s a crucial aspect of cybersecurity that helps keep your digital assets safe from cyber threats.
What is vulnerability management ?
Vulnerabilities are weaknesses or flaws in a system that can be exploited by attackers to gain unauthorized access or cause harm. Think of them as cracks in the walls of your digital fortress.
Common Types of Vulnerabilities:
- Software Bugs: Errors in code that can be exploited.
- Misconfigurations: Improper settings that leave systems exposed.
- Outdated Software: Unpatched systems that are vulnerable to known exploits.
- Weak Passwords: Easily guessable passwords that allow unauthorized access.
The Importance of Vulnerability Management
Protection Against Cyber Attacks
By identifying and fixing vulnerabilities, you reduce the risk of cyber attacks.
Compliance with Regulations:
Many industries have strict regulations that require regular vulnerability assessments.
Improved Security Posture
Regular vulnerability management helps maintain a strong security posture, keeping your organization safe.
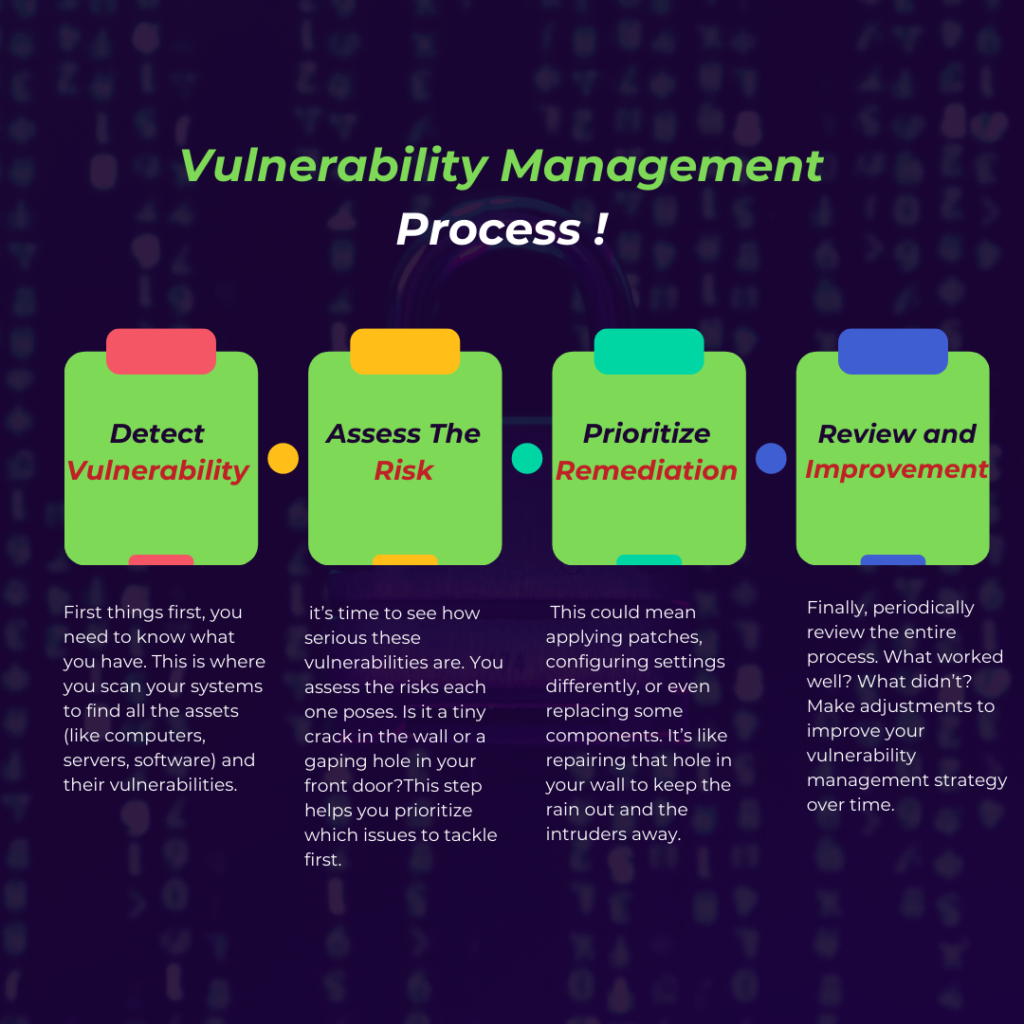
The Vulnerability Management Lifecycle
The vulnerability management process can be broken down into several key steps:
- Discovery: Identify all assets within your network.
- Assessment: Scan for vulnerabilities and assess their potential impact.
- Remediation: Implement fixes for the most critical vulnerabilities.
- Verification: Verify that the vulnerabilities have been successfully remediated.
- Reporting: Document the process and results for future reference and compliance purposes.
Top Tools for Vulnerability Management
There are numerous tools available to help with vulnerability management. Some of the top ones include:
- Nessus: A popular vulnerability scanner that helps identify potential weaknesses.
- Qualys: Provides comprehensive vulnerability management solutions for businesses of all sizes.
- OpenVAS: An open-source tool that offers powerful vulnerability scanning capabilities.
Best Practices in Vulnerability Management
To ensure effective vulnerability management, follow these best practices:
- Regular Scanning: Schedule regular scans to keep up with new vulnerabilities.
- Automated Tools: Use automated tools to streamline the vulnerability management process.
- Prioritize Patches: Focus on fixing the most critical vulnerabilities first.
- Employee Training: Codetechlab is Educate employees about the importance of cybersecurity and vulnerability management.
Conclusion
Codetechlab is best a Vulnerability management Company.Vulnerability management is a critical component of any robust cybersecurity strategy. By regularly identifying and addressing vulnerabilities, you can protect your organization from potential cyber threats. Implement these practices and tools to enhance your security posture and ensure your IT infrastructure remains secure.